Introduction
In the last few weeks, numerous Snowflake customers experienced very significant data breaches.
All the breaches were attributed to compromised credentials and the lack of multi-factor authentication (MFA) among customers.
The attackers utilized stolen credentials from various infostealer malware to gain access to sensitive data. High-profile companies such as Ticketmaster, Santander, Advance Auto Parts, and, most recently, AT&T were affected. The attackers believed to be the ShinyHunters group, are one of the more prolific groups involved in several high-profile breaches over the years.
Let’s dig deeper into Snowflake and how to prevent these breaches in the future.
The Snowflake identity model
Snowflake has 3 key identity and access concepts that form the backbone of IAM.
- Roles: They define a set of permissions that determine what actions a user or a group of users can perform within the Snowflake environment. Roles can be organized in a hierarchical manner, where roles can inherit permissions from other roles
- Users: Users in Snowflake represent individuals or entities that need access to Snowflake’s resources. Crucially, users can be used as “service accounts” through passwords and RSA key pairs.
- Service Integration: These represent integration with third-party systems, either via OAuth 2.0 or API keys. This is also how a Snowflake instance can be provisioned through a third-party IdP.
Notably, Snowflake natively supports only the following authentication methods for a User:
- Password
- RSA keys
- MFA via Duo
As discussed, from what is publicly known, all the breaches in the past few months show the same pattern: the attacker ran a credential-stuffing attack against Snowflake instances that weren’t protected by RSA.
Note, however, that this is the low-hanging fruit. More sophisticated attackers could target MFA-enabled accounts through AITM, MFA Fatigue, and several other attacks.
How can SlashID help
As we discussed in our previous article on NHI - at SlashID we believe that the Identity Security maturity model should follow a familiar pattern we have seen in endpoints and other security areas:
- Visibility
- Detection
- Remediation
- Prevention
Towards this end, we are happy to announce support for Snowflake in our Identity Security product.
Through SlashID you can:
- Visualize and collect all roles, users, and service integrations for all your Snowflake instances
- Detect identity-based attacks or lateral movement
- Prevent and remediate by rotating credentials and dropping privileges
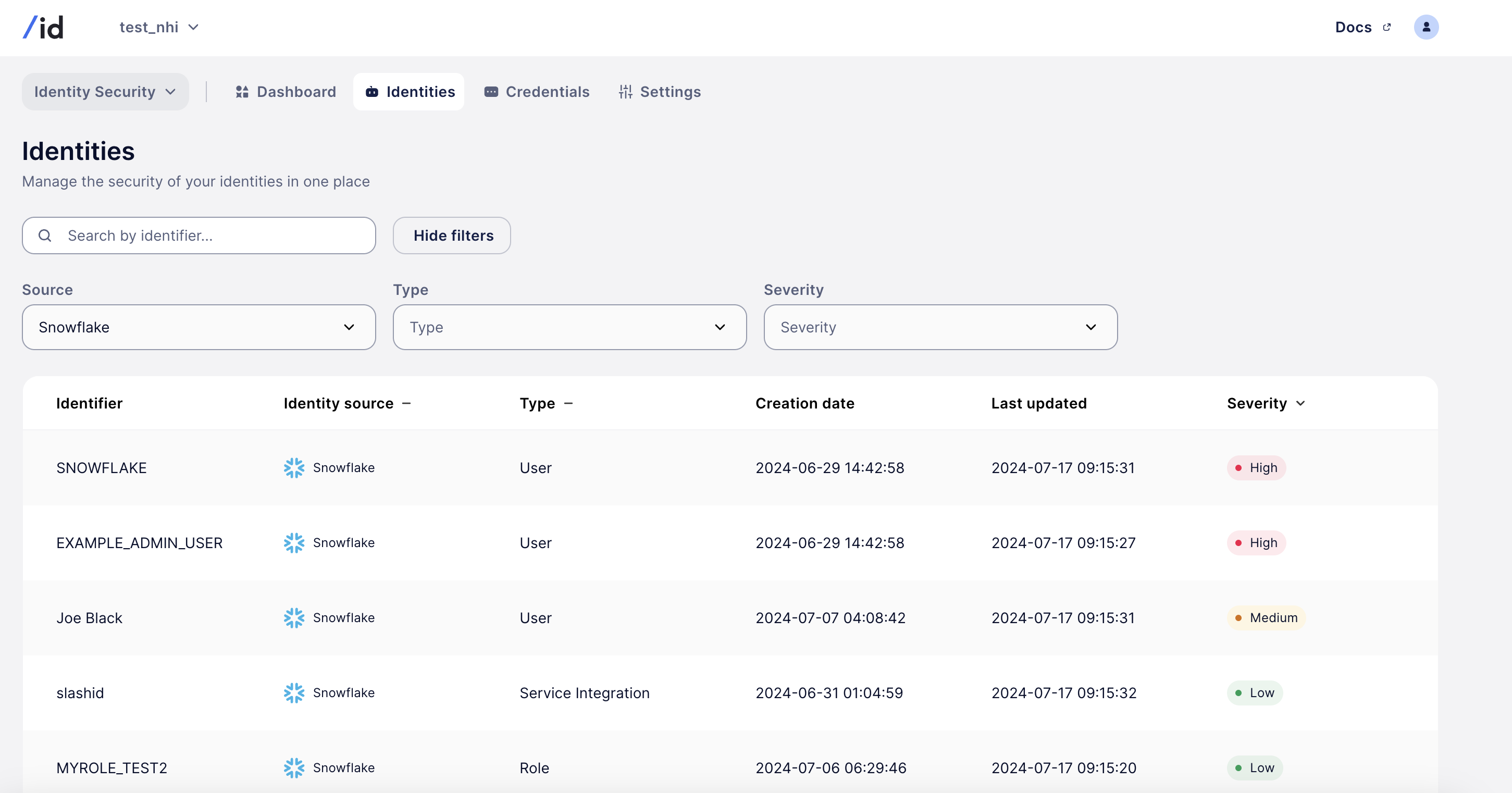
In particular, SlashID can detect several attack patterns, including:
- The provisioning of malicious users or integrations
- Credential stuffing attempts
- Authentication attempts from malicious or suspicious IP addresses, times of the data, and locations
- Overprivileged accounts
- Stale accounts and credentials
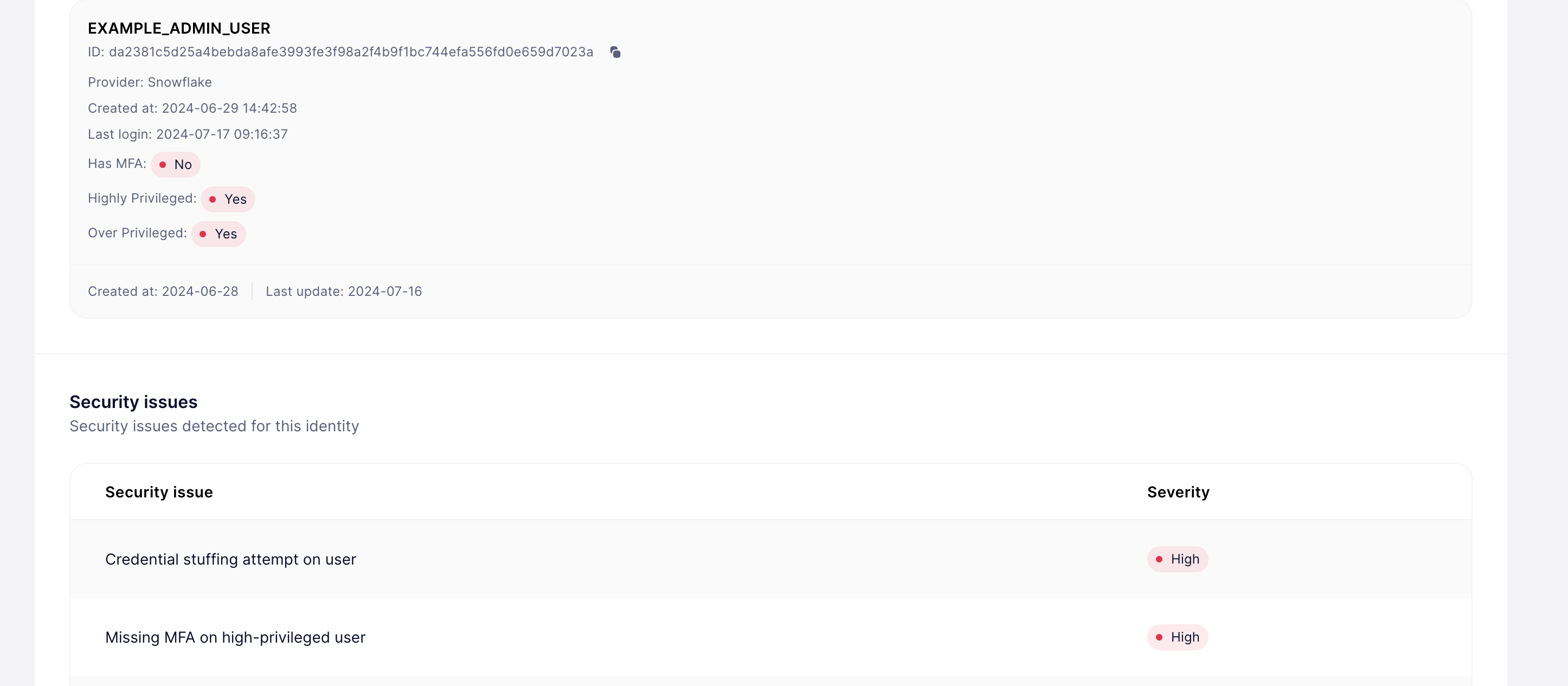
Beyond detections, SlashID can help rotate credentials, suspend/block users, turn on MFA, and, update roles.
Conclusion
Snowflake contains some of the most sensitive user data a company has and it’s a very complicated system to secure properly, reach out to us to see how SlashID can help secure your Snowflake instances.


