The Problem SlashID is Solving
According to Verizon’s Data Breach Investigation Report, stolen credentials accounted for approximately 40% of breaches in 2023. One of the most common techniques to steal credentials is a man-in-the-middle (MITM) or adversary-in-the-middle (AITM) attack.
A (MITM) attack happens when a threat actor inserts themselves between two parties (often a user and an application), intercepting and/or altering the communication between the two for malicious purposes, such as stealing payment information or making unauthorized purchases. Today there is an abundance of readily available tools to do just that and performing an attack using an MITM proxy has become almost trivial, with evilnginx2 and modlishka being two of the more popular frameworks.
Implementing a robust detection mechanism is essential to prevent a potential breach or remediate an ongoing one, and that’s where SlashID can help you with the new MITM detection capability.
Read on to learn how to detect MITM proxy attacks on your websites or third-party Identity Providers and applications with SlashID.
Enable MITM Detections on your Website
First, you need to create an MITM token in the SlashID Console. You will need to provide:
- a list of allowed domains your application can be accessed on
- a tag that will be included in any detections to easily identify which of your applications was attacked
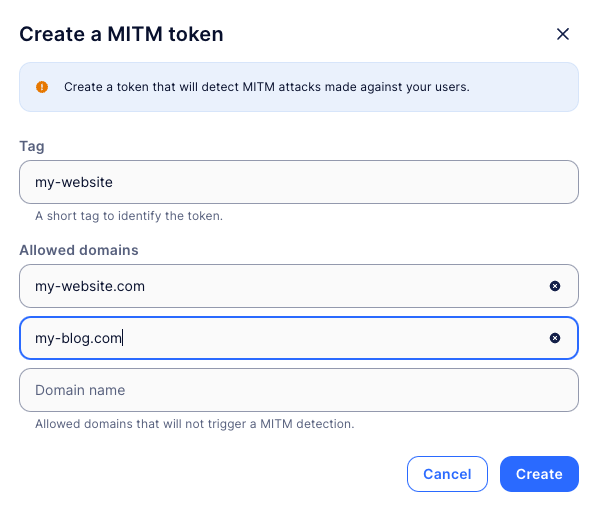
Once you submit this information, SlashID will generate an MITM token that you can embed in your website as a single line of html:
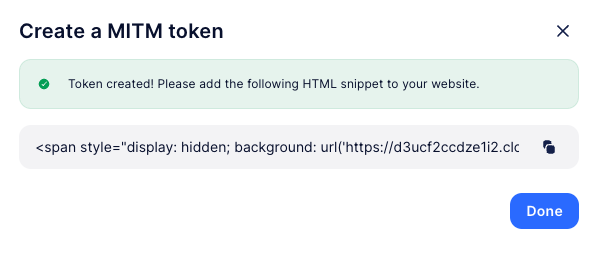
And that’s it: SlashID will now detect MITM attacks performed by proxying your application from a domain not explicitly allowed in the MITM token you just created.
Identity provider integrations
Login pages of well-known Identity providers can also be a target of an MITM proxy attack. SlashID can help you detect these attacks by embedding the MITM token in the custom CSS or HTML of the login page. Here we outline how to set this up for Okta and Microsoft Entra ID.
Okta
Okta allows customizing their sign-in page with a code editor, assuming that you configured a custom domain for the sign-in page.
This integration requires the following steps:
- ensure a custom domain is set up in order to enable the code editor
- ensure the Content Security Policy will allow downloading images from
https://d3ucf2ccdze1i2.cloudfront.net - use the code editor to add the SlashID MITM token HTML snippet anywhere within the
bodyelement
Microsoft Entra ID
Microsoft Entra ID allows uploading custom CSS to style the sign-in page. In this case, we cannot use the full HTML snippet. Instead, we’ll use only the relevant CSS property - background: url('{MITM_TOKEN}.png' and apply it using a selector of your choice:
- start from the reference company branding CSS template
- write a rule consisting of one of the documented selectors and the
background: url('{MITM_TOKEN}.png'property - upload the custom CSS file
MITM Attack Visibility
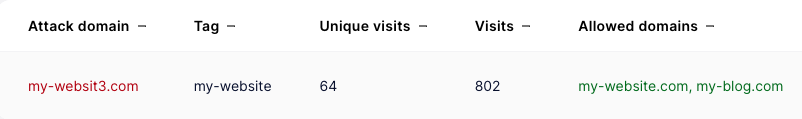
When a detection is triggered, it will be displayed in the SlashID Console, showing you the MITM token tag, the domain that is proxying requests, and the number of visits (total page loads and unique visits based on the IP address):
If you want to be notified of MITM attacks as they happen, you can use SlashID webhooks. Any time a website with a SlashID MITM token is accessed via a malicious proxy, your webhook will receive an event with the following information:
- IP address of the user accessing the page
- the user-agent string
- the attack domain
- the allowed domains
- token tag
Early detection allows you to respond promptly by notifying the affected parties, blocking the malicious proxy, or implementing additional security measures that prevent further compromise.
Try it out!
Protect your website against Man-in-the-Middle attacks by signing up for a free SlashID account and following the simple steps outlined in this blog post.